Exposure management - Managing assets, attack surface, attack paths, and vulnerabilities with purpose
There are a variety of cybersecurity product categories and activities intended to reduce the likelihood that an adversary finds and successfully exploits a vulnerability, resulting in an intrusion (and ultimately a breach):
- Asset management (often including “inventory”)
- Attack surface management
- Attack path management
- Vulnerability management
- And more . . .
In thinking about how all of these fit, and in particular what a vertically integrated product or activity might look like, I find it helpful to think about the attributes or unique set of attributes that matter the most. In the context of assets that comprise our attack surface, any of which may have a number of points of vulnerability and thus be subject to attack, the attribute that seems to matter most is exposure.
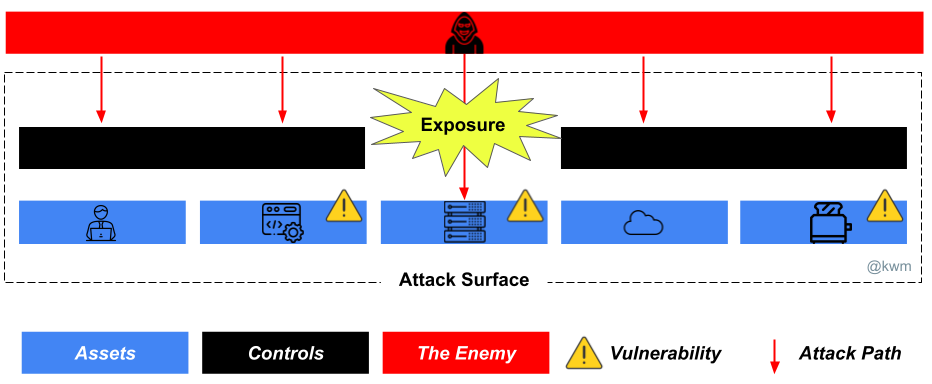
You can have assets rife with vulnerabilities, but through a variety of controls make those vulnerabilities inaccessible enough (or contain the system such) that you have mitigated or deprioritized the risk. At the same time, you can have an asset with a single esoteric vulnerability, and if that vulnerability is exposed you can end up in a very serious situation.
Exposure management is the act of looking at your attack surface in the proper context to identify the subset of assets that are exposed–meaning that a vulnerability is exploitable by an adversary—so the corresponding risk can be mitigated or remediated. For example:
- Threat intelligence is used to identify the highest likelihood and highest impact threats, and to ensure that risks to assets are tracked, understood, and actioned if necessary. It’s worth noting that exploitability of a vulnerability is a critical aspect of threat intelligence for this particular purpose. For example: Knowing that ransomware is a threat is obviously helpful. Knowing that a ransomware actor gains access through a software vulnerability with a publicly or commercially available exploit meaningfully impacts prioritization.
- Data from technical controls will help to make determinations about which assets and corresponding vulnerabilities are reachable in the first place and/or whether there are mitigations in place. There’s a huge opportunity to better correlate data from endpoint, cloud, and application security products to make these determinations.
- Lastly, but arguably most important, is using every piece of data and information at your disposal to ensure that you have the most complete picture of your attack surface. Unmanaged assets are the adversary’s plaything.
Naturally, the productization of this concept in any vertically integrated manner–meaning combined data, information, and intelligence spanning each of these areas–would move the needle in a manner that is more actionable, leading to better outcomes likely at a lower cost.
And in general, instead of trying to optimize for completeness or maturity in any or all of these areas on their own, consider how you might do just enough of each with a high degree of coordination, and in doing so actively and effectively reduce risk by managing your exposure.
