The most prolific ransomware groups in 2022
It’s 2023 and security firms are starting to release findings from 2022 threat data, notably their lists of the most active, impactful ransomware groups.
As with all threat reports, the findings and prevalence are subject to each firms’ visibility, methodology, etc. The data isn’t perfect and it’s not particularly actionable on its own, but it’s interesting and in aggregate can be a useful starting point for other types of analysis.
The leaderboard
This is not the product of original intelligence analysis. I’ve aggregated data from reports that contain ransomware group rankings, assigned points based on relative ranking, and this is the result.

Read on for some thoughts re: how this type of data can be useful, followed by summary data and charts from each report.
The case for imperfect threat data
A good use case for these types of lists–and a way to make them actionable–is to look at tactics starting with initial access and progressing through the intrusion lifecycle. For each tactic, look for common vectors and MITRE ATT&CK techniques (some of this is readily available in the source reports below). The goal is to see whether we can glean good enough insights and do it quickly, assess risks, and take preventative measures.
This sounds simple and obvious because it is. The short list of “how ransomware happens” isn’t terribly long and few TTPs are novel. Unfortunately, it’s easy and common for teams to get wrapped up in the minutiae of threat modeling, risk quantification, etc.–perfect over plenty good enough–and in doing so they waste valuable time addressing high impact, high likelihood risks that are staring us right in the face.
Reports and summary data
Coalition, Inc
- ALPHV/BlackCat
- LockBit
- Royal
- Hive
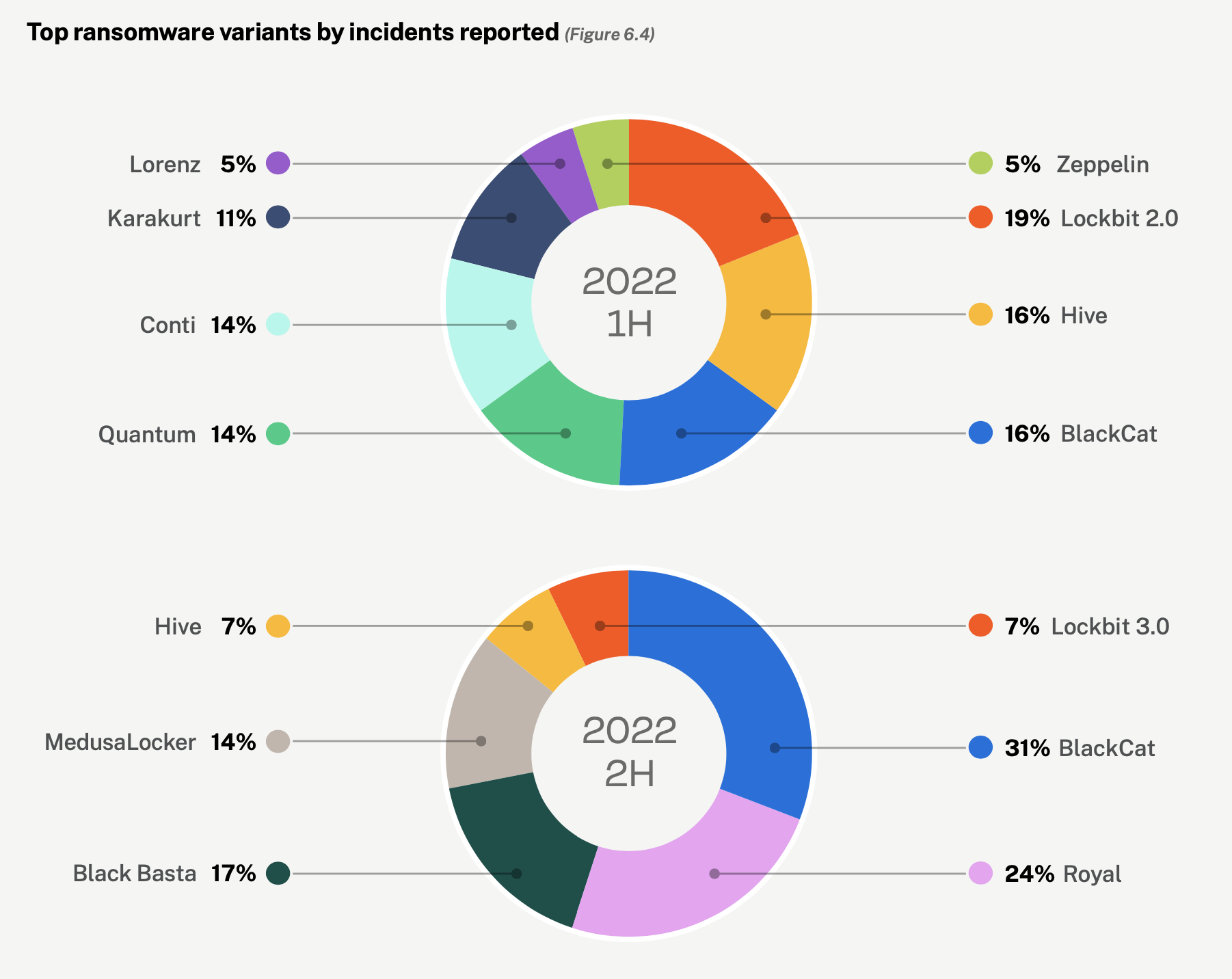
IBM X-Force
- LockBit
- Phobos, WannaCry (tie)
- ALPHV/BlackCat
- Conti, Djvu, Babuk (tie)
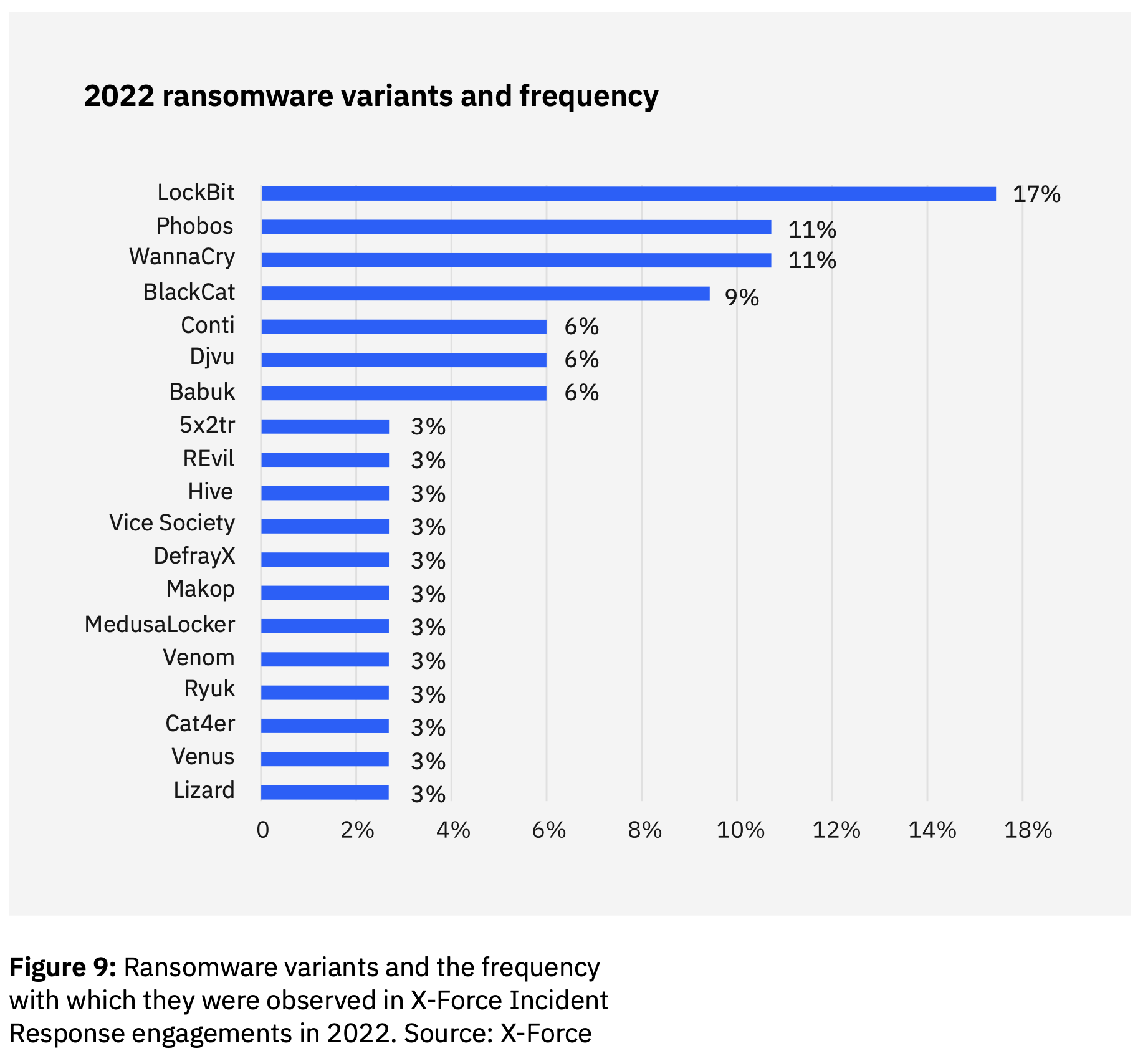
Intel471
- LockBit 2.0
- LockBit 3.0
- ALPHV/BlackCat
- Black Basta
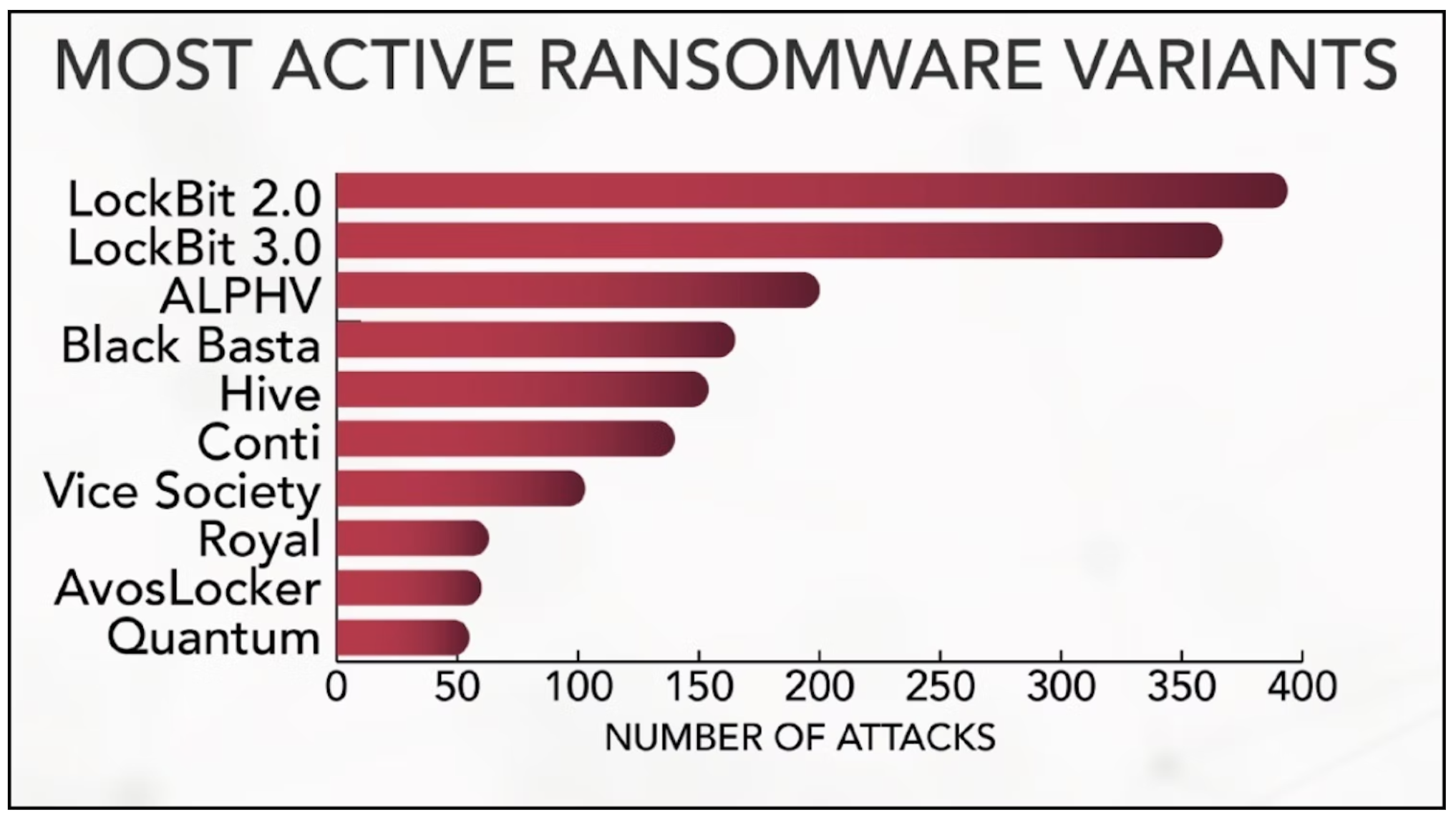
GuidePoint
- LockBit
- ALPHV/BlackCat
- Hive
- Black Basta
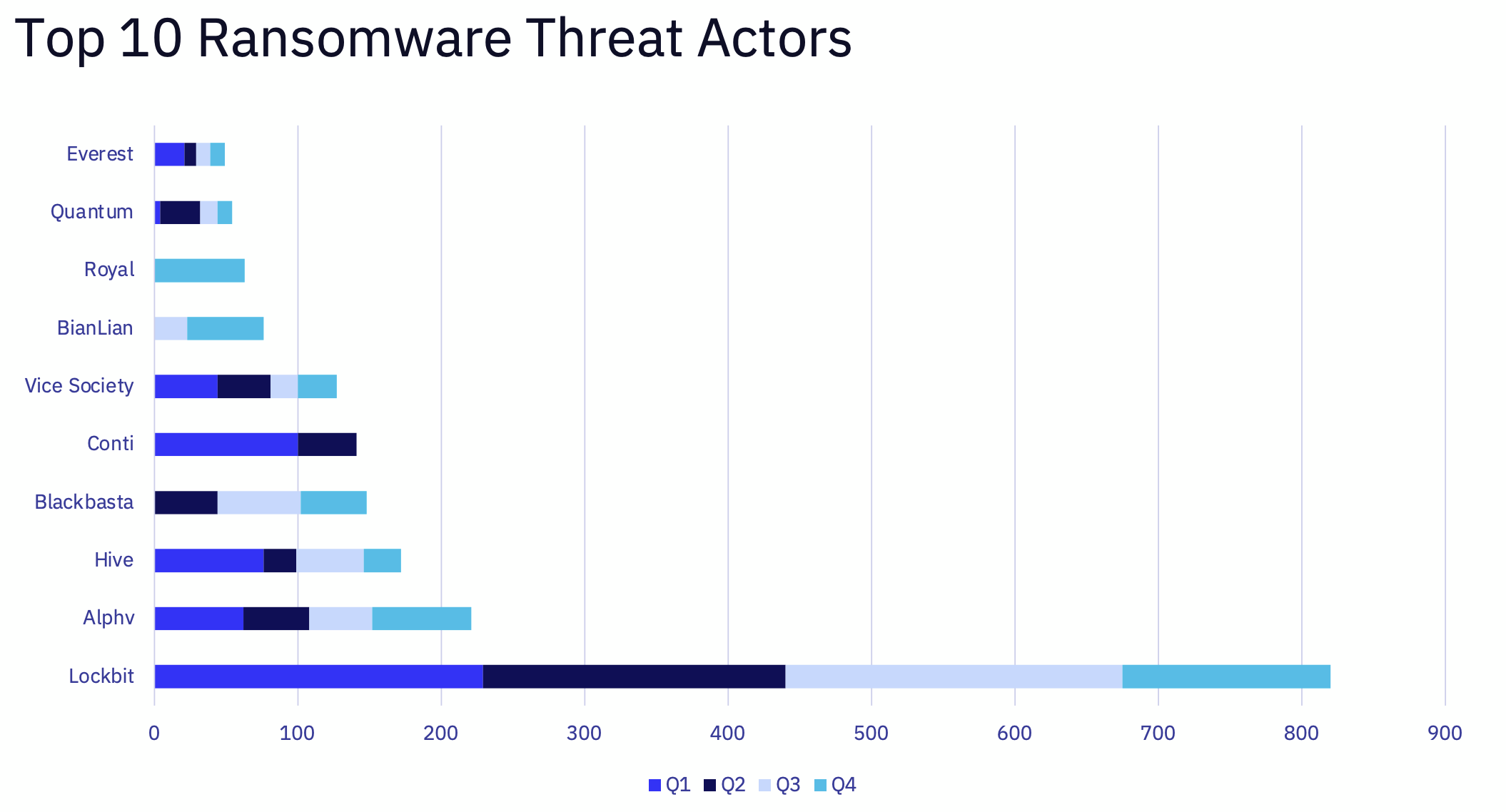
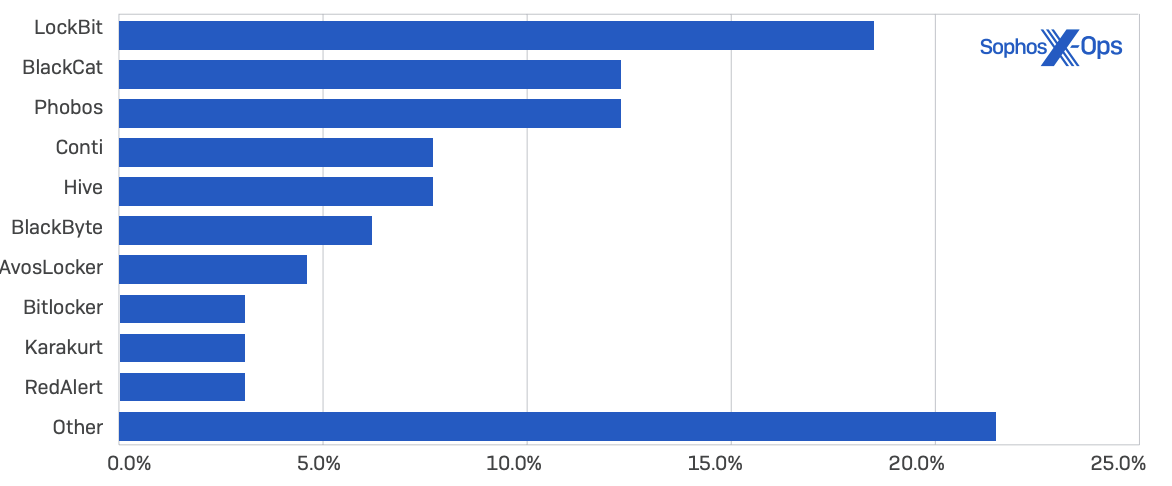
Sophos
- LockBit
- ALPHV/BlackCat
- Phobos
- Conti
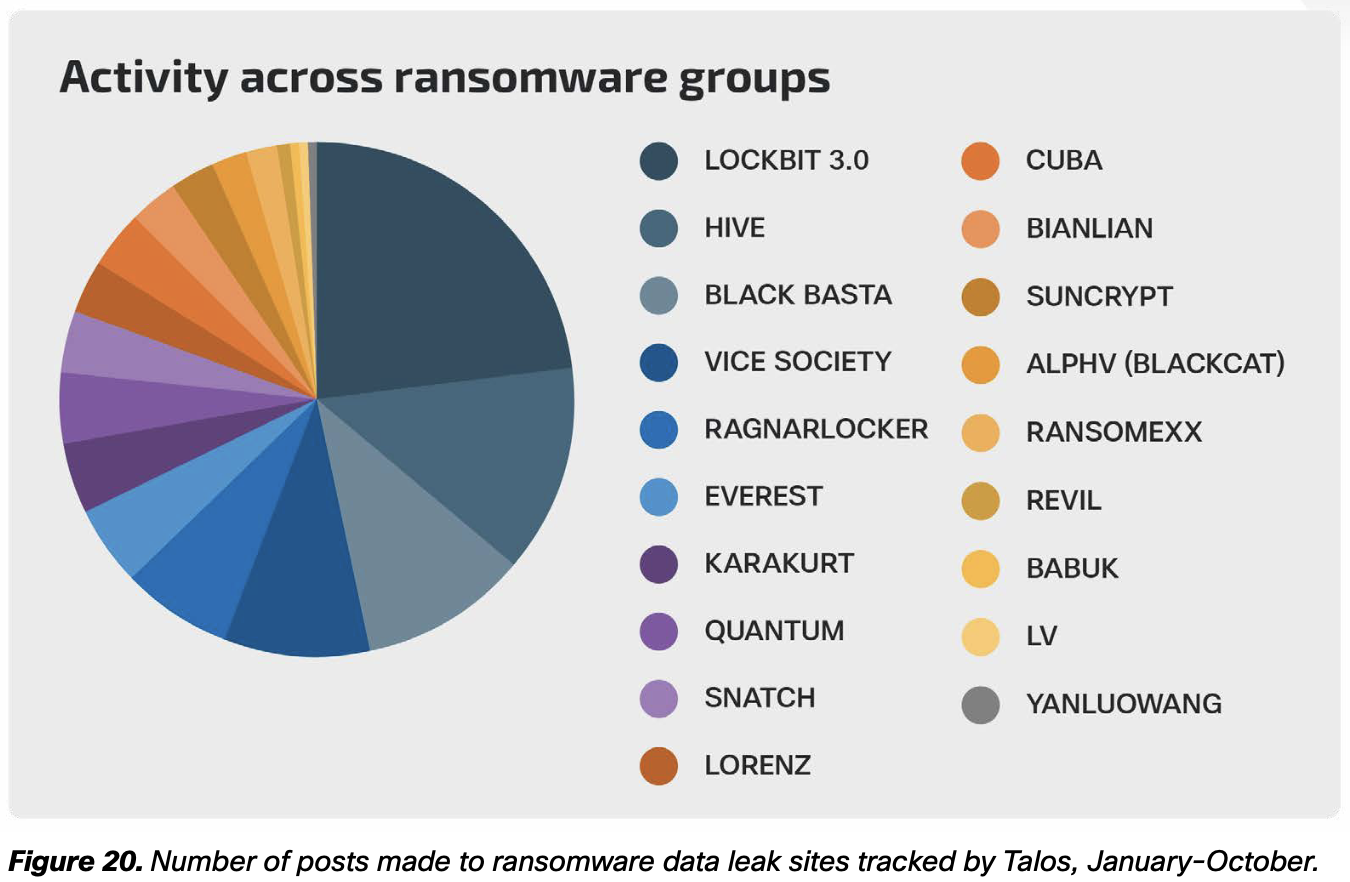
Cisco Talos
- LockBit
- Hive
- Black Basta
- Vice Society
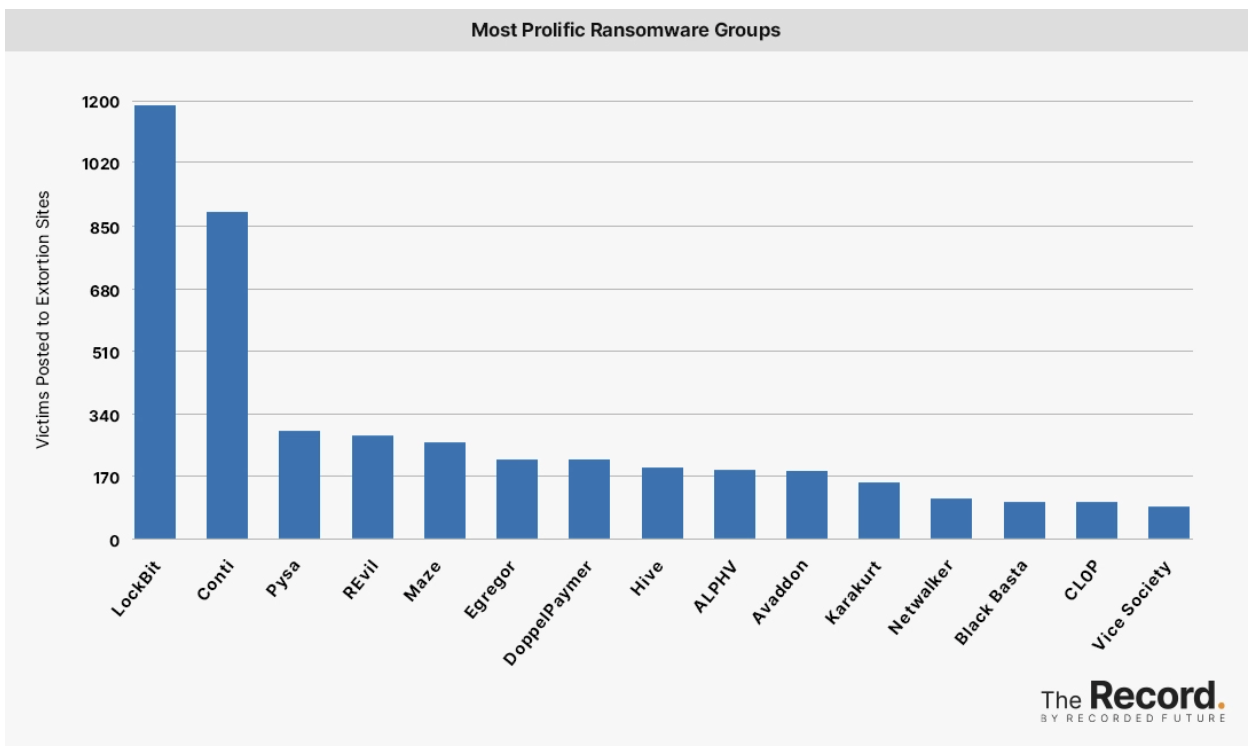
Recorded Future
- LockBit
- Conti
- Pyaa
- REvil
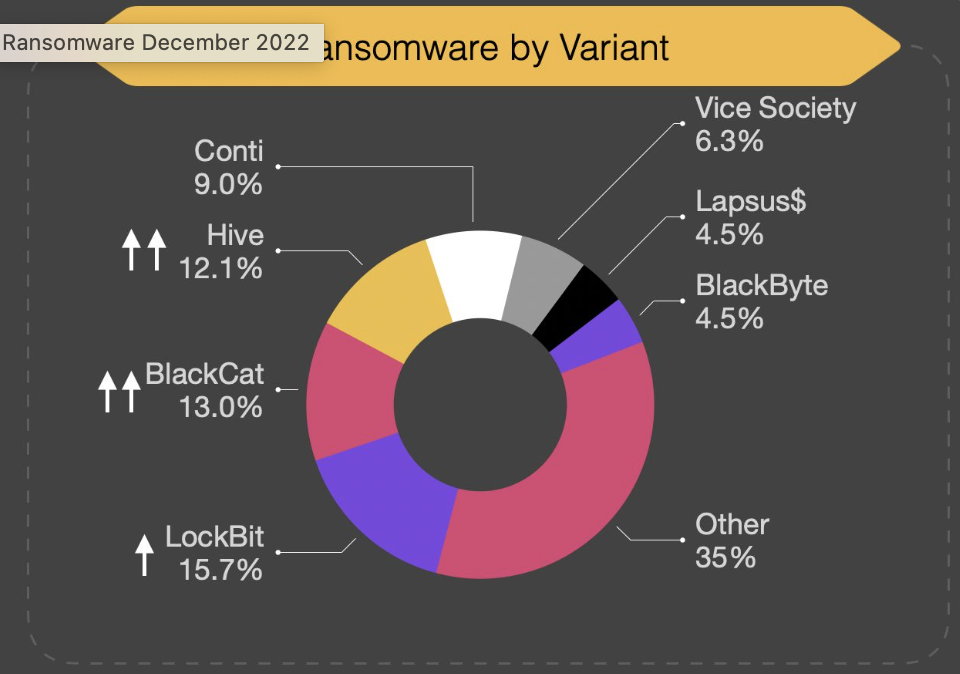
BlackFog
- LockBit
- ALPHV/BlackCat
- Hive
- Conti
TrustWave
- LockBit
- Black Basta
- Hive
- ALPHV/BlackCat
