Trust and the cybersecurity buyer’s journey
The buyer’s journey is a common framework for understanding how customers (who have problems) find products provided by vendors (to address problems).
- Awareness - Knowing that a problem and potential solutions exist. Brand awareness is a key component of this stage.
- Consideration - Which potential solutions are you considering?
- Evaluation - Of the solutions being considered, how do they stack up? Feature comparisons, pros and cons, and other criteria are examined.
- Purchase - A solution is chosen and purchased. This stage is also referred to as “Adopted.”
- Post-Purchase - The solution is implemented. Critically, it’s here that the customer makes some early and important determinations with regards to how the solution performs relative to their expectations and the vendor’s promises during Evaluation.
What’s unique about the security industry?
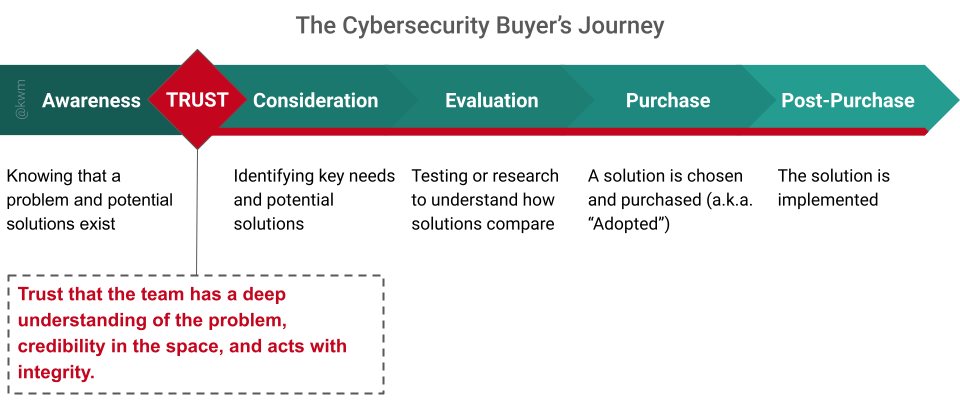
Put simply: The security industry is grounded in the principle of trust:
- Trust that the team has a deep understanding of the problem, credibility in the space, and acts with integrity.
When companies purchase virtually any other type of technology, they tend to seek out specific functionality, can easily determine whether the product works as intended, and may have an interest in the roadmap but aren’t dependent on future functionality for their success.
When we purchase security products—particularly those that we rely on to perform critical operational functions—our journey is unique:
- We want some specific functionality (e.g., reporting, interoperability), but what we really want is an outcome (e.g., a net reduction in harmful emails delivered to users).
- While we typically have some tests that we can use to validate that the system works as intended, we can be assured that the system will face an endless barrage of inputs designed by a capable actor to avoid detection.
- We often have a keen interest in the vision and roadmap as a bellwether for the team’s depth of understanding, commitment, and ability to productize or operationalize threat intelligence findings (i.e., as adversaries evolve, will the product evolve to meet them, and do so in a timely manner?).
Major features we’ll try to discern early on by way of the website, webinars, and other public materials. Efficacy we can test superficially during an evaluation. But oftentimes we won’t get to Evaluation (or even Consideration) unless we have a good sense for whether the team understands the problem and has credibility in the space—key ingredients of trust. Most of the time, we’ll have a sense for this as (or before) we begin this journey, by virtue of personal or professional networks, conferences, and published research.
Also note that trust in the team can absolutely compensate for lack of features, or even some lack of efficacy. Cybersecurity is an adversarial discipline, and great products work a great percentage of the time, but nothing’s perfect. A trustworthy and capable team will shine in the face of failure, responding with transparency and decisive action.
This concept is important to leaders because trust, inclusive of credibility and integrity, are virtually impossible to fake or decide on a whim that you want. The behaviors and principles that lead to trust either come naturally to founders and early employees, and are integral to company culture, or they are not. And ultimately, despite how nice your product and marketing look, security practitioners are looking through these things to determine whether and to what degree they trust your team to deliver on an ongoing basis against a determined and skilled adversary.
