Breaking down exposure management
While participating in some industry analyst research, I was asked how I’d walk someone through and connect these concepts. This is a paraphrased version of the talk track (with some visuals based on prior work).
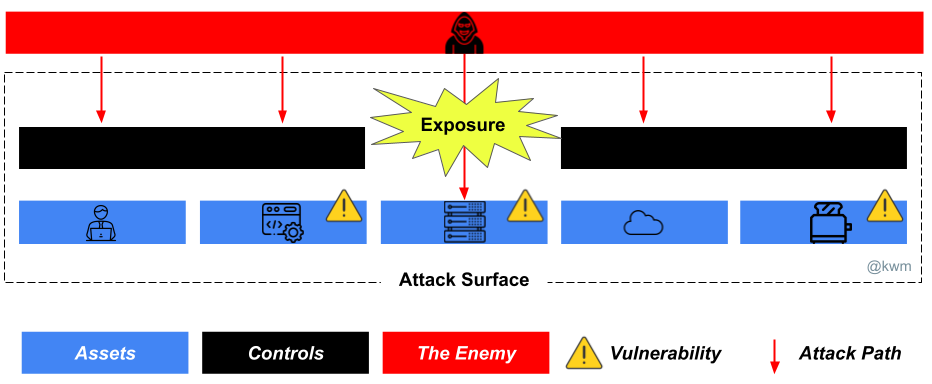
I’ve continued to think about the convergence of a number of foundational security activities into a more holistic exposure management practice (and ultimately, exposure management products). Those activities include, asset, attack surface, attack path, and vulnerability management, among others. In this case, we’ll look at them hierarchically.
Situational awareness: Assets and attack surface
Asset management is foundational to information technology governance and cybersecurity hygiene. We often say that we can’t detect what we can’t see, but this overlooks the fact that we can’t do anything at all to protect an asset that we don’t know about in the first place. Asset management takes into account the subjects of processes like procurement, ownership, maintenance, periodic inventory or other forms of discovery, and more. Of course, not all assets that an organization will manage are cybersecurity or information assets, but it’s better to be greedy when it comes to intake of asset data, so that you can exclude assets that aren’t in scope versus making assumptions.
Every asset management activity is an opportunity to identify and manage your attack surface.
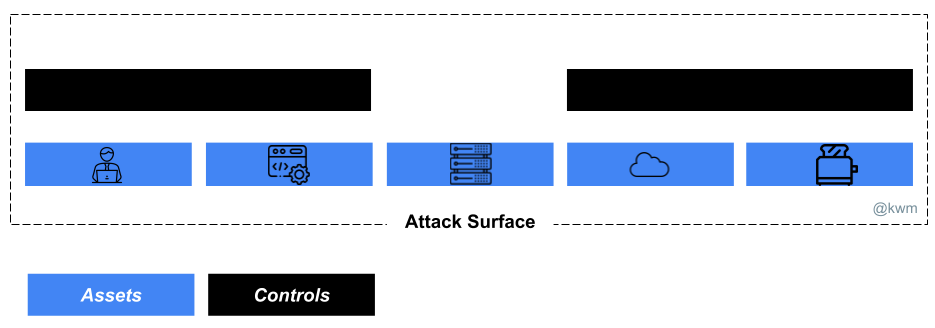
Attack surface management involves continually validating the presence, state, and key attributes of assets you know about, and actively seeking assets you don’t yet know about or understand (i.e., assets not captured as part of asset management processes). The goal of this activity is to enrich your asset data set with the information needed to know what needs protecting, and ultimately to continuously take the steps needed to protect at-risk assets.
Your security controls are part of your attack surface!
Attack surface management may be best thought of as an umbrella activity within which a number of lower-level, highly conextual activities exist.
Context and depth: Attack paths, vulnerabilities, intelligence, and more
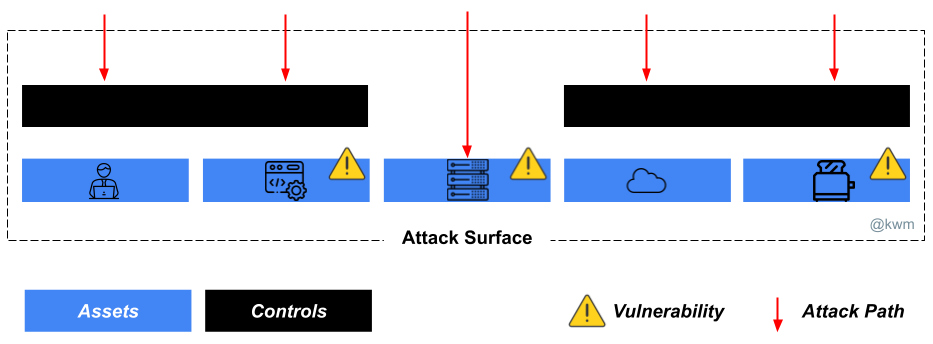
Attack path management, which starts with how an adversary might gain initial access to any part of our attack surface, and progresses into understanding the various ways they can progress by way of identities, applications, systems, networks, and more. This can range from very simple to very in-depth:
- Elementary: Understanding asset accessibility. For instance, are assets accessible only via internal networks, or are they connected directly to the Internet? Are web-based portals also protected by key material, or can anyone access the login screen?
- Intermediate: Understanding asset components and behavior? What does the system look like when observed under normal operating conditions? What user, application, or underlying platform behaviors might be present if it is under attack?
- Advanced: Understanding the asset in the context of a holistic threat model, including whether the system is subject to targeting by adversaries with exceptional capabilities or motivations.
Vulnerability management, best thought of as a peer to attack path management, as most initial access stems from some identified and manageable class of vulnerability, including software, configuration, process, or human/user.
Good attack surface management solutions also incorporate ongoing activities like network scanning and cloud posture management (technically a form of configuration vulnerability management). They also includes oversight activities like penetration testing and red teaming, aimed at validation assumptions about your attack surface and your ability to defend it against adversaries.
Ultimately, the synthesis of all of this data integrated with high quality threat intelligence, to help you prioritize what’s likely and understand what’s possible, should result in understanding which of your assets are most exposed so that you can take action to mitigate risk.