The top initial access vectors in 2022, mapped to ATT&CK
This data is from 2022. For data from 2023 (the most recent), please go HERE.
In reviewing security firms’ 2022 threat data, a subset of these include insight into the initial access vectors leveraged most frequently in successful intrusions. This is a summarization of findings based on their reporting.
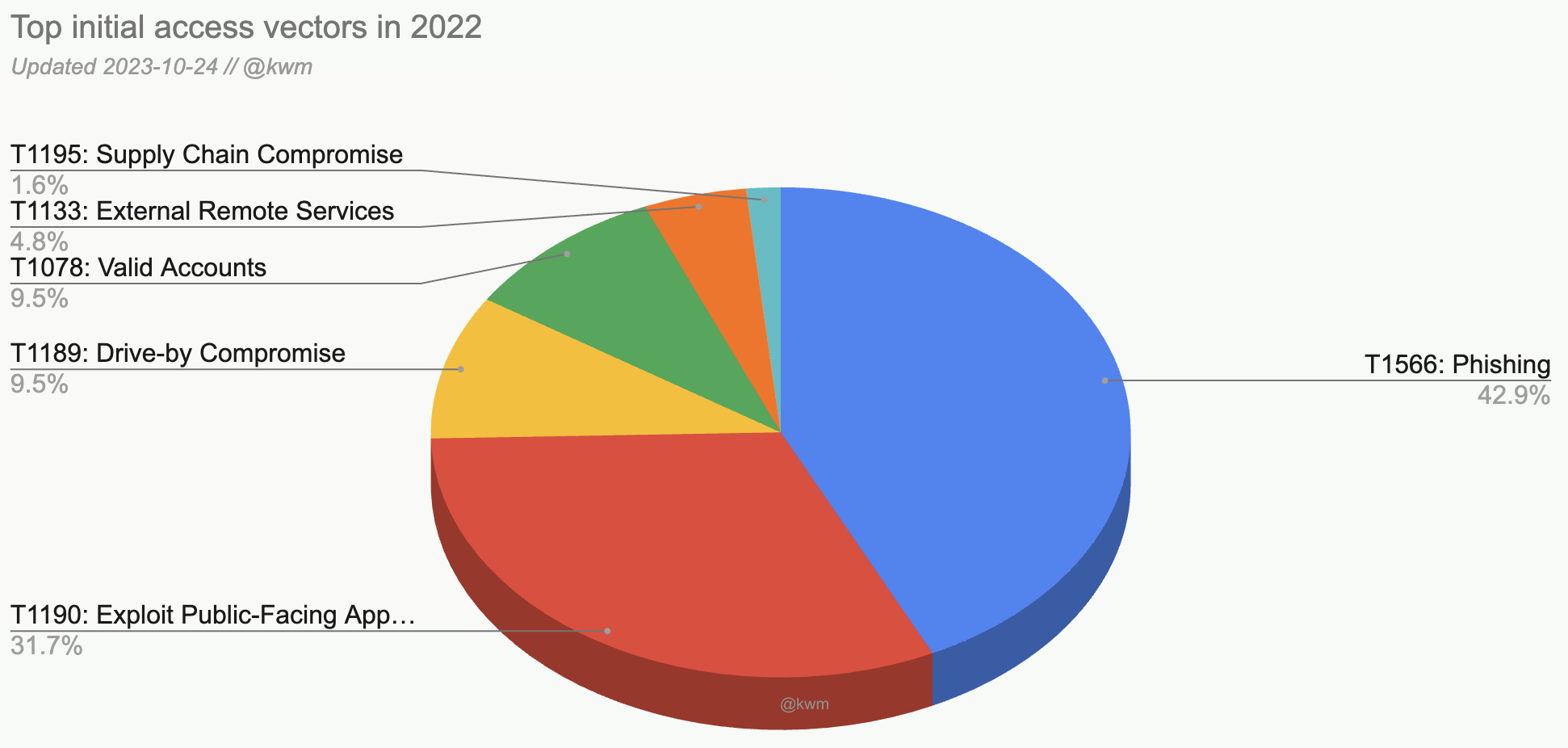
| Rank | MITRE ATT&CK Technique ID | Vector | Percentage |
|---|---|---|---|
| 1 | T1566 | Phishing | 42.9% |
| 2 | T1190 | Exploit Public-Facing Application | 31.7% |
| 3 | T1189 | Drive-By Compromise | 9.5% |
| 3 | T1133 | Valid Accounts | 9.5% |
| 4 | T1078 | External Remote Services | 4.8% |
| 5 | T1195 | Supply Chain Compromise | 1.6% |
Methodology
To determine the most prevalent initial access techniques leveraged by adversaries in 2022, I relied on data from the following reports:
- eSentire 2023 Ransomware Report: Disrupting Initial Access
- HP Wolf Security Threat Insights Report Q4 2022
- IBM Security X-Force Threat Intelligence Index 2023
- Kaspersky Nature of Cyberincidents 2022
- Kroll Q4 2022 Threat Landscape
- Mandiant M-Trends 2023
- NCC Group Annual Threat Monitor 2022
- Secureworks Learning from Incident Response: 2022 Year in Review Report
Because not all of these reports use a standard taxonomy, reported vectors were mapped to the corresponding MITRE ATT&CK Initial Access parent technique.
As with all threat reports, the findings and prevalence are subject to each firms’ visibility and methodology.
How to use this information
From my earlier thoughts on this matter:
A good use case for these types of lists–and a way to make them actionable–is to look at tactics starting with initial access and progressing through the intrusion lifecycle. For each tactic, look for common vectors and MITRE ATT&CK techniques (some of this is readily available in the source reports below). The goal is to see whether we can glean good enough insights and do it quickly, assess risks, and take preventative measures.
