The top initial access vectors in 2023, mapped to ATT&CK
In reviewing security firms’ 2023 threat data, a subset of these include insight into the initial access vectors leveraged most frequently in successful intrusions. This is a summarization of findings based on their reporting.
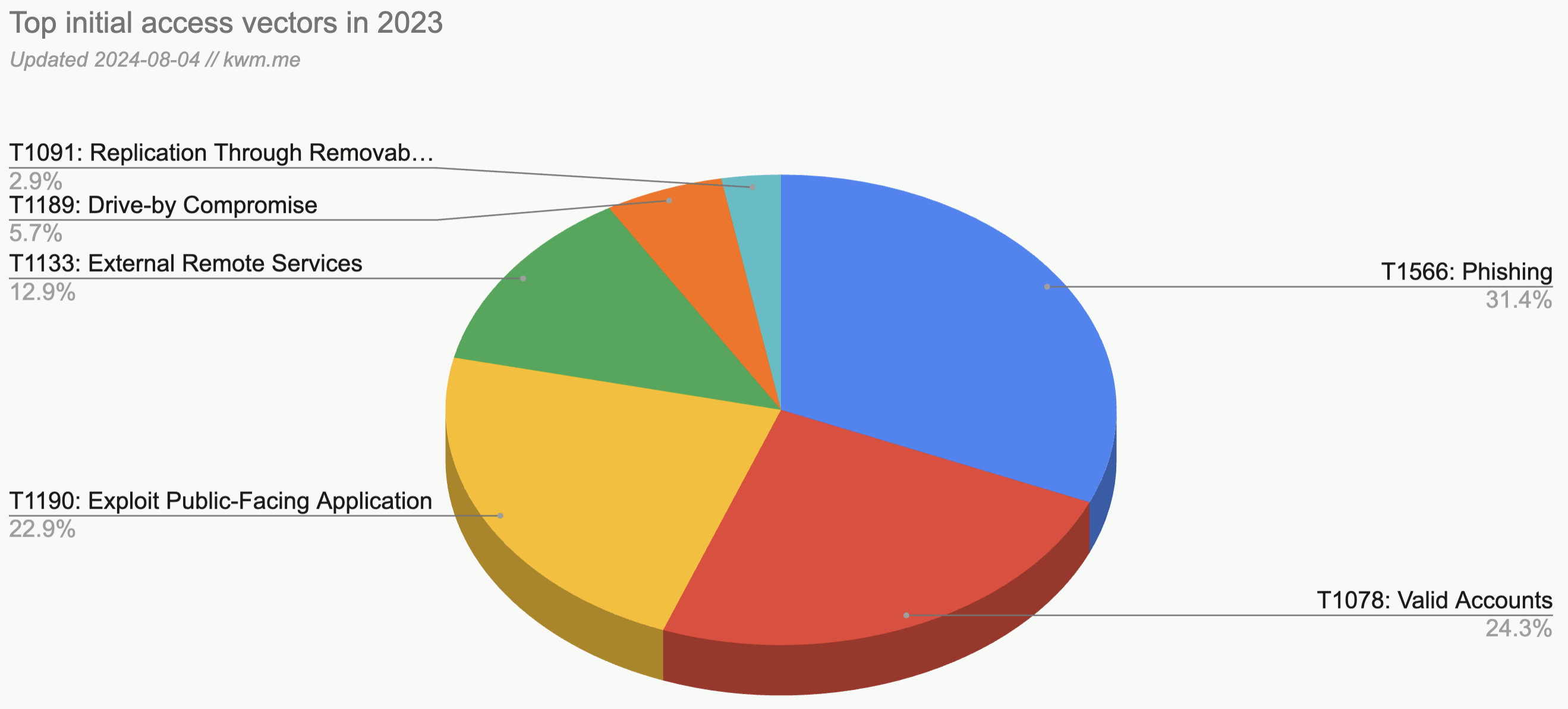
| Rank | MITRE ATT&CK Technique ID | Vector | Percentage |
|---|---|---|---|
| 1 | T1566 | Phishing | 31.4% |
| 2 | T1078 | Valid Accounts | 24.3% |
| 3 | T1190 | Exploit Public-Facing Application | 22.9% |
| 4 | T1133 | External Remote Services | 12.9% |
| 5 | T1189 | Drive-By Compromise | 5.7% |
| 6 | T1091 | Replication Through Removable Media | 2.9% |
Key takeaways
- The top 5 of the 6 most prevalent initial access techniques were unchanged from 2022, despite some new reporting sources being introduced in 2023 and some 2022 sources being excluded. The underscores the fact that, like the most prevalent techniques across tactics, there continues to be relatively little year-over-year drift.
- Despite the ascendency of Valid Accounts and External Remote Services, and Exploit Public-Facing Application holding ground, it’s not always Phishing, but Phishing still dominates as the most likely initial access technique and email remains the vector of choice for adversaries.
- Valid Accounts surged from 9.5% and a three-way tie for 3rd in 2022 to a solid #2 in 2023.
- External Remote Services, which may be attributable to widespread remote access and/or RMM abuse, more than doubled year-over-year.
Methodology
To determine the most prevalent initial access techniques leveraged by adversaries in 2023, I relied on data from the following reports:
- Deloitte Cybersecurity Threat Trends Report 2024
- IBM Security X-Force Threat Intelligence Index 2024
- Kaspersky IR Analyst Report 2023
- Kroll Q4 2023 Threat Landscape
- Mandiant M-Trends 2024
- ReliaQuest Annual Cyber-Threat Report: 2024
- Secureworks (multiple reports, best found via search-fu)
Because most, but not all of these reports use a standard taxonomy, reported vectors were mapped to the corresponding MITRE ATT&CK Initial Access parent technique.
As with all threat reports, the findings and prevalence are subject to each firms’ visibility and methodology.
Notes on 2023 data on reporting
Vendors in general are shifting away from annual reporting in favor of periodic reporting, with quarterly reports becoming the most common. This complicates data aggregation a bit (e.g., see the link required to find and aggregate Secureworks reports), but may be more useful to practitioners, as trends at a quarterly level are probably based on enough data to be meaningful, while also being timely.
Fewer vendors are reporting initial access observations. Fortunately, there are some industry mainstays that continue to report high quality data in this area based on large samples year-over-year.
I was disappointed to see that NCC Group, which generally provides excellent public domain research and reporting, not only stopped reporting initial access data this year, but also didn’t make mention of a single MITRE ATT&CK technique or provide standardized data anywhere in their annual report.
How to use this information
From my earlier thoughts on this matter:
A good use case for these types of lists–and a way to make them actionable–is to look at tactics starting with initial access and progressing through the intrusion lifecycle. For each tactic, look for common vectors and MITRE ATT&CK techniques (some of this is readily available in the source reports below). The goal is to see whether we can glean good enough insights and do it quickly, assess risks, and take preventative measures.
